
© 2019 - 2023 Rakovsky Stanislav

© 2019 - 2023 Rakovsky Stanislav

Article about forgering metadata on PyPI.org

PHDays 12 + Python Conf++ about ways how threat actors forge their packages metadata

Webinar about securing yourself from malicious python packages
UPD 9 feb: An article on habr

THE OFFZONE 2022 speech about threat actors trying to infect developers in Python Package Index.
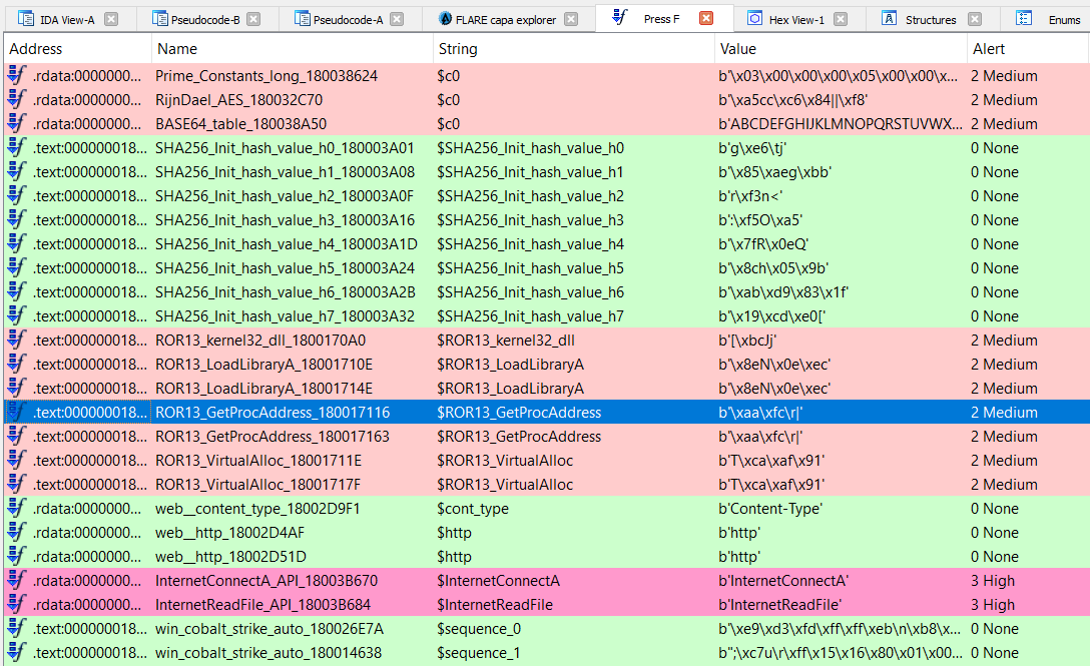
I was a speaker at spbctf summer 2021 meetups with brief talk about currently available static methods for analysis executable files that will be helpful in CTF/MA reverse process.
A link to youtube (ru) - Currently unavailable.

THE STANDOFF 2021 speech about multifunctional backdoor Forest Keeper. It belongs to Chinese APT group that targets Russia.

I reviewed the trends of 2020 and 2021 in the use of PyInstaller in malware. I provided statistics on the versions used, analysis of mechanisms for gaining persistence in the system, data theft, encryption, and communication with C&C. Special attention to obfuscation and how to deal with it.
Recourses from my PHDays 10 speech.
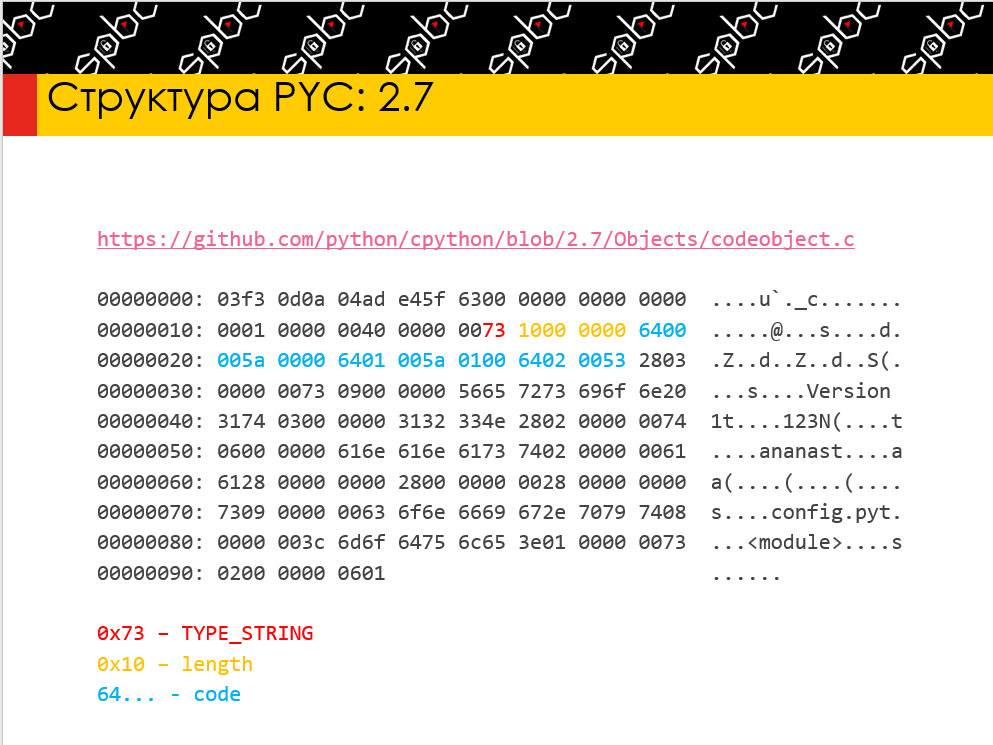
I was a speaker at spbctf NY 2020 meetups with my research about possibilities of reverse PYC (compiled python) files, paths how to obfuscate it to complicate the work of reverse engineers, hehe. And, finally, how to investigate obfuscated pycs.
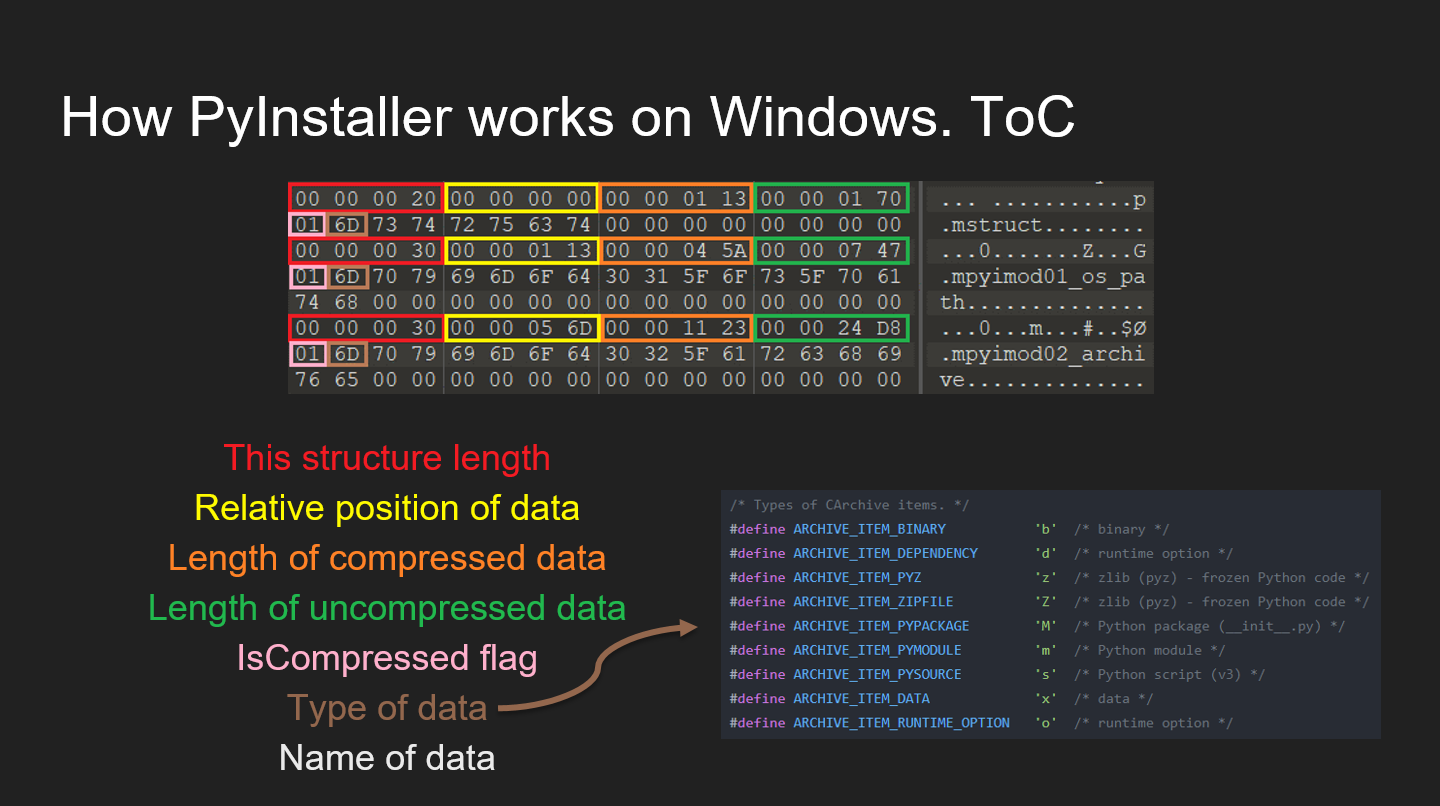
Recourses from my THE STANDOFF 2020 speech.
The main goal of my research was analysing attack vectors on PyInstaller and check the possibility to inject our payload to each of them.
Under construction
Hello from another side of the Moon!
Looking for a flag? Okay, take this:
LFXXKIDBOJSSA43XMVSXIIC6LYQCAIA=
Under construction. You can try to contact me and fill this field… haha… ha…