reverse, easy > Baby rev
EZ task for beginners in RE.
Don't forget to add ctfzone and curly braces before submitting flag (like ctfzone{FLAG_HERE}).
There is a MS-DOS binary file.
The _main function is located at seg000:13DB
It has a pretty cute tricking option. It:
- says
This program cannot be run in DOS mode. - sleeps 5 seconds (
0x1388) - sets foreground color to green
- clears the console
- and then makes its work
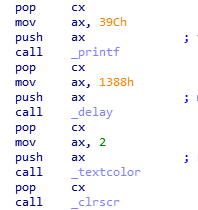
This behaviour may confuse the beginner reverser :3
The next things are loop initialisation code (blue), reading from the file (purpre) and the chain of checks (yellow).
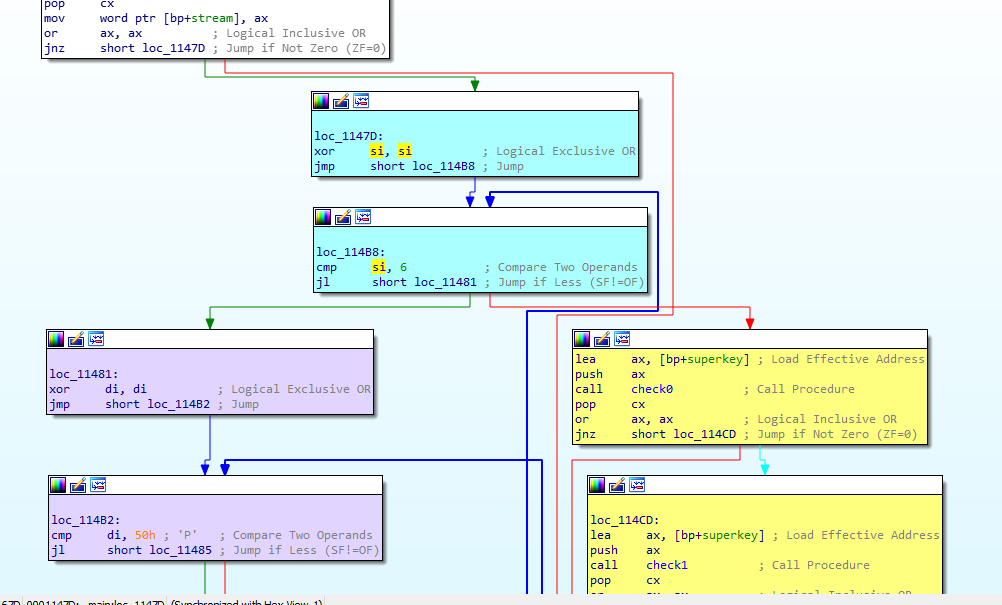
There are 8 similar functions (i named them check0 - check7) that look like a big if-else chain.
It checks each byte from our input file using si register as base address. Let’s write the idapython script to parse them all:
from idautils import *
from idaapi import *
si = {}
ea = BeginEA()
for funcea in Functions(SegStart(ea), SegEnd(ea)): # walk through all the functions
functionName = GetFunctionName(funcea)
if "check" in functionName:# if the function name contains "check"
print(functionName)
for (startea, endea) in Chunks(funcea):
for head in Heads(startea, endea):
if GetMnem(head) == "cmp" and "si" in GetOpnd(head, 0): # if it's an operation "cmp" with si register
val = int(GetOpnd(head, 1).replace("h", ""), 16)
if "[si]" in GetOpnd(head, 0):
si.update({0:val})
continue
offs = GetOpnd(head, 0)
offs = offs[offs.index("+")+1:offs.index("]")].replace("h", "")
si.update({int(offs, 16):val})
#print functionName, ":", "0x%08x"%(head), ":", GetDisasm(head), ":"
print si
print "1 Ok"
t = list(si.keys())
t.sort()
m = "".join([chr(si[i]) for i in t])
with open("out", "w") as f:
f.write(m)
print "2 Ok!"
Okay! How it looks:
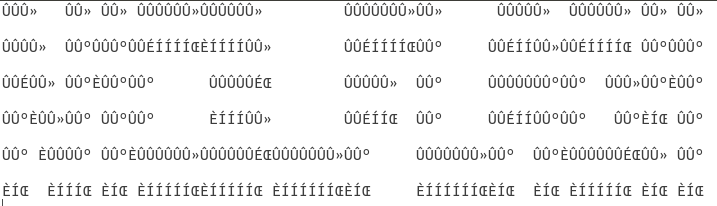
Let’s type out flag using dos (I actually wrote the flag from the text, @silmaulviel said about type command)

Tip of the day:
Functions _print and _put take the string from dseg section.
mov ax, 374h; start of “This program…” string in dseg
push ax
call _print
author, editor: Rakovsky Stanislav, Unicorn CTF